JOIN OUR AUTOMOTIVE CYBERSECURITY MASTERY PROGRAM
• Cybersecurity for Embedded Software Design & Architecture •
• ISO/SAE 21434 Comprehensive Training •
• Introduction to Applied Cryptography •
• Secure Coding •
• Penetration Testing •
• Automotive Cybersecurity Crash Course •
*Special offer for a limited time
Did you know that the Global Automotive Cybersecurity Market is expected to grow up to $9.7 billion by the year 2030?
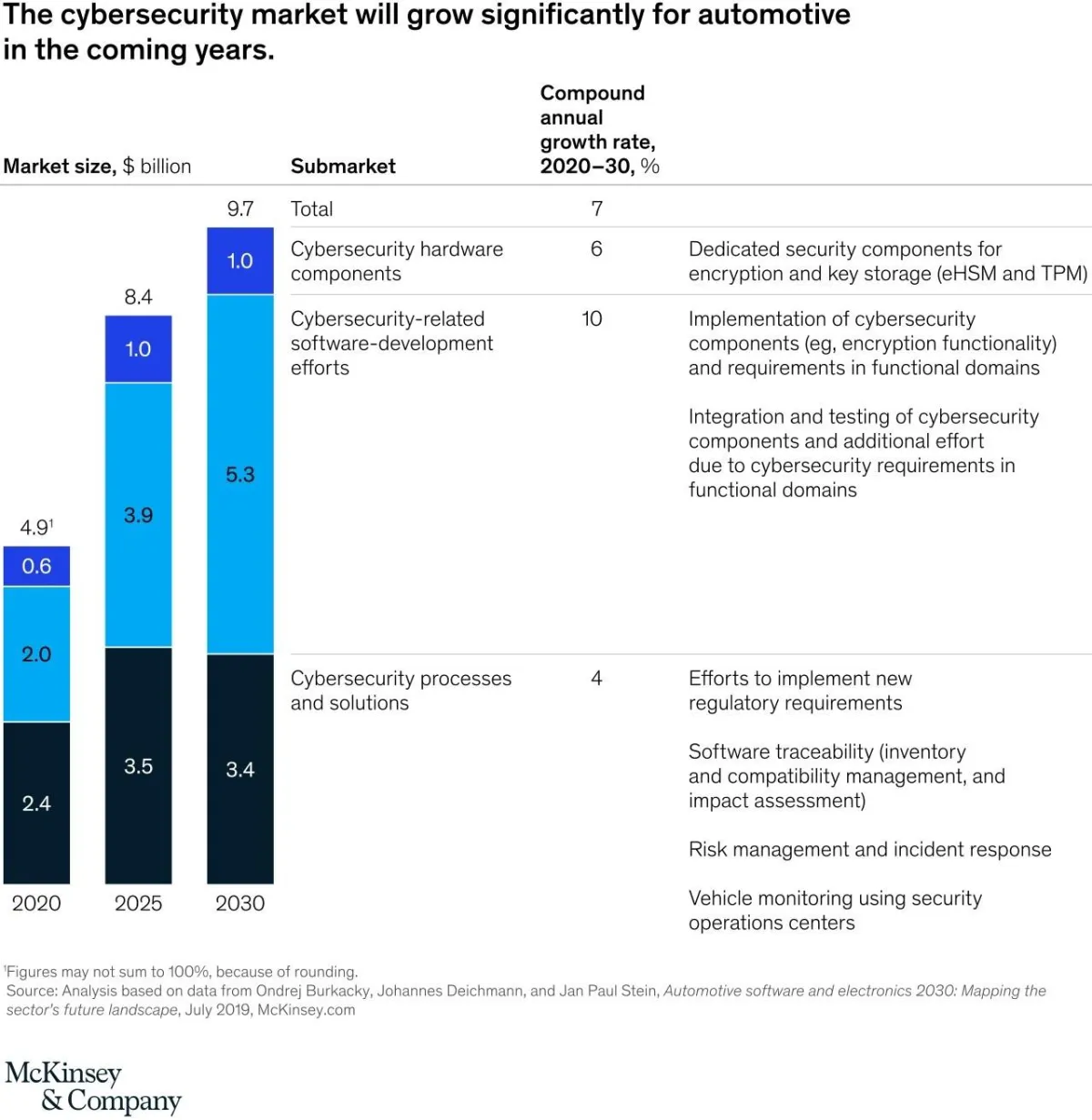
Now is your chance to make a big move forward in your career.
Don't miss the chance!
Meet your automotive cybersecurity mentor

Hello, aspiring cybersecurity students!
My name is Dr. Hasan Ibne Akram.
I am the CEO of Matrickz GmbH, a Munich-based company specializing in automotive software and security. My specialization is on Embedded Security and Machine Learning.
I am also a computer scientist, podcaster, speaker, and serial entrepreneur, but this time, I will be with you on your journey in Automotive Cybersecurity.
OUR COURSES IN THE AUTOMOTIVE CYBERSECURITY MASTERY PROGRAM
What you'll learn
Cybersecurity for Embedded Software Design & Architecture
Start Date: Aug 24, 31, Sep 6, Sep 7, 2024
Time: 4 PM CET - 8 PM CET (4 hours each day)
Total Duration: 16 hours
Prerequisite: Automotive Cybersecurity Crash Course
Course Outline:
Module 1: Cybersecurity Requirements in Software Engineering
Importance of Security Requirements in Secure Software Development
Identifying Security Requirements based on Threat Models and Risk Assessments
Methods for Deriving and Documenting Secure Requirements
Module 2: Designing Secure Software Architecture
Principles and Best Practices of Secure Software Architecture for Automotive Systems
Applying Secure Architecture Patterns and Strategies (e.g., Least Privilege, Separation of Duties)
Secure Communication Mechanisms and Data Protection Strategies
Module 3: Practical Exercise: Developing a Secure Software Architecture
Participants will design a secure system architecture for a given automotive scenario (e.g., Telematics Unit)
Group Discussion and Feedback on Designed Architectures
Module 4: Integrating Advanced Security Mechanisms
Hardware Security Modules (HSM) and their role in Automotive Systems
Over-The-Air (OTA) Updates and Security Considerations
Secure Onboard Communication (SecOC) Protocols and Implementations
Integrating Cryptography for Secure Data Communication and Storage
Module 5: Practical Exercise: Implementing Security Mechanisms
Participants will practice integrating chosen security features (HSM, OTA, SecOC) into their designed architectures
Collaborative problem-solving and troubleshooting exercises
Module 6: Secure Coding Guidelines and Best Practices
Writing Secure Code for Automotive Applications
Mitigating Common Coding Vulnerabilities (e.g., Buffer Overflows, SQL Injection)
Secure Coding Standards and Best Practices for Automotive (e.g., MISRA C)
Module 7: Practical Exercise: Secure Coding
Participants will apply secure coding principles in a coding activity focused on automotive functionalities
Peer code review and discussion to identify and address potential security issues
Module 8: Introduction to Cybersecurity Testing
Fundamental Security Testing Strategies for Automotive Software
Overview of Testing Tools and Techniques used in Cybersecurity
Module 9: Cybersecurity Testing in Practice
Conducting Static and Dynamic Security Tests on Automotive Software
Case Studies and Analysis: Examining real-world examples of security vulnerabilities and their impact
Module 10: Overview of Penetration Testing
Planning and Executing Penetration Tests for Automotive Systems
Practical Considerations for Conducting Ethical Hacking

ISO/SAE 21434 Comprehensive Training
Start Date: November 12, 16, 23, 25, 27, 29, 2024
Time: 4 PM CET - 8 PM CET (4 hours each day)
Total Duration: 24 hours
Prerequisite: None
Course Outline:
Module 1: Introduction to ISO/SAE 21434 and Automotive Cybersecurity
Challenges in Automotive Cybersecurity
Fundamentals of Cybersecurity
Fundamentals of Automotive Cybersecurity
Module 2: Overview of ISO/SAE 21434
Purpose of the ISO/SAE 21434 standard
Cybersecurity in the context of road vehicles
Overview of document structure
Reference to ISO 21434: Introduction and Scope (Clause 1, 2 and 3)
Module 3: General Considerations
Context and perspective on automotive cybersecurity engineering
Application limits of the document
Relation to other cybersecurity and functional safety standards
Reference to ISO 21434: General Considerations (Clause 4)
Module 4: Organizational Cybersecurity Management
Cybersecurity governance
Cybersecurity culture
Information sharing
Management systems
Tool management
Information security management
Organizational cybersecurity audit
Reference to ISO 21434: Organizational Cybersecurity Management (Clause 5)
Module 5: Project-dependent Cybersecurity Management
Cybersecurity responsibilities
Cybersecurity planning
Tailoring
Reuse
Component out-of-context
Off-the-shelf component
Cybersecurity case
Cybersecurity assessment
Release for post-development
Reference to ISO 21434: Project-dependent Cybersecurity Management (Clause 6)
Module 6: Distributed Cybersecurity Activities
Supplier capability for cybersecurity
Request for quotation (RFQ)
Alignment of cybersecurity responsibilities
Reference to ISO 21434: Distributed Cybersecurity Activities (Clause 7)
Module 7: Continual Cybersecurity Activities
Cybersecurity monitoring
Cybersecurity event evaluation
Vulnerability analysis
Vulnerability management
Reference to ISO 21434: Continual Cybersecurity Activities (Clause 8)
Module 8: Concept Phase
Item definition
Cybersecurity goals
Cybersecurity concept
Reference to ISO 21434: Concept Phase (Clause 9)
Module 9: Product Development
Design
Integration and verification
Reference to ISO 21434: Product Development (Clause 10)
Module 10: Cybersecurity Validation
Strategies for validating cybersecurity at the item level
Integration of cybersecurity validation into overall vehicle validation
Reference to ISO 21434: Cybersecurity Validation (Clause 11)
Module 11: Production
Cybersecurity considerations in manufacturing and assembly processes
Quality assurance for cybersecurity in production
Reference to ISO 21434: Production (Clause 12)
Module 12: Operation, Maintenance, and Service
Cybersecurity incident response
Cybersecurity Updates
Reference to ISO 21434: Operation and Maintenance (Clause 13)
Module 13: End of Life and Decommissioning
Secure decommissioning practices
Management of cybersecurity risks during decommissioning
Reference to ISO 21434: Decommissioning (Clause 14)
Module 14: Threat Analysis and Risk Assessment Methods
Asset identification
Threat scenario identification
Impact rating
Attack path analysis
Attack feasibility rating
Risk value determination
Risk treatment decision
Reference: Threat Analysis and Risk Assessment Methods (Clause 15)

Introduction to Applied Cryptography
Start Date: December 26,27,28 & 29, 2024
Time: 4 PM CET - 8 PM CET (4 hours each day)
Total Duration: 16 hours
Prerequisite: None
Course Outline:
Module 1: Introduction to Cryptography
What is cryptography and its importance in automotive cybersecurity?
Core cryptographic concepts: confidentiality, integrity, authentication, non-repudiation.
Overview of cryptographic primitives: encryption, decryption, hashing, digital signatures.
Module 2: Symmetric Key Cryptography
Introduction to symmetric key algorithms (e.g., AES, DES)
Block ciphers and stream ciphers: principles and operation modes.
Key management considerations for symmetric encryption in automotive systems.
Module 3: Asymmetric Key Cryptography
Introduction to public-key cryptography (PKI) and key pairs.
Understanding digital certificates and their role in authentication.
Public-key algorithms (e.g., RSA, Elliptic Curve Cryptography) and their applications.
Module 4: Digital Signatures and Message Authentication
Digital signature schemes and their properties.
Hashing functions and their role in digital signatures.
Message authentication codes (MAC) and their use in automotive communication.
Module 5: Cryptographic Applications in Automotive Cybersecurity
Securing communication channels using TLS/SSL and secure in-vehicle communication protocols.
Protecting software updates and data integrity using digital signatures.
Key management strategies for automotive systems (e.g., Hardware Security Modules).
Module 6: Cryptographic Vulnerabilities and Mitigations
Common cryptographic weaknesses (e.g., brute-force attacks, side-channel attacks).
Secure coding practices for cryptographic implementations.
Importance of algorithm selection and key size based on security requirements.
Module 7: Case Studies and Real-World Applications
Exploring real-world applications of cryptography in automotive systems (e.g., keyless entry, secure boot).
Analyzing case studies of cryptographic vulnerabilities in automotive security breaches.
Module 8: Wrap-Up and Q&A
Summary of key concepts and best practices.
Q&A session to address participant questions and real-world scenarios.

Secure Coding
Start Date: December 2,3,4 & 5, 2024
Time: 4 PM CET - 8 PM CET (4 hours each day)
Total Duration: 16 hours
Prerequisite: None
Course Outline:
Module 1: Introduction to SEI CERT Coding Standards
Lesson 1
- Overview of Software Engineering Institute (SEI) and CERT
- Importance of secure coding standards
- Common security vulnerabilities in software development
- Introduction to SEI CERT coding standards and their purpose
Module 2: SEI CERT C Coding Standard
Lesson 2
- Introduction to the CERT C coding standard
- Key principles and guidelines in CERT C
Lesson 3
- Common vulnerabilities in C and how CERT C mitigates them
- Detailed study of specific CERT C rules and recommendations:
* Rule EXP00-C: Do not use invalid pointers
* Rule STR31-C: Guarantee that storage for strings has sufficient space for character data and the null terminator
* Rule MSC32-C: Properly seed pseudo-random number generators
Lesson 4
- Hands-on exercises:
* Identifying and fixing vulnerabilities in sample C code
* Applying CERT C guidelines to improve code security
Module 3: SEI CERT C++ Coding Standard
Lesson 5
- Introduction to the CERT C++ coding standard
- Key principles and guidelines in CERT C++
Lesson 6
- Common vulnerabilities in C++ and how CERT C++ mitigates them
- Detailed study of specific CERT C++ rules and recommendations:
* Rule DCL50-CPP: Do not define a C-style variadic function
* Rule EXP61-CPP: A lambda object must not outlive any of its reference captured objects
* Rule CTR50-CPP: Guarantee that container indices and iterators are within the valid range
Lesson 7
- Hands-on exercises:
* Identifying and fixing vulnerabilities in sample C++ code
* Applying CERT C++ guidelines to improve code security

Penetration Testing
Start Date: September 13, September 20 & September 29, October 6, 2024
Time: TBA 8 hours each day
Total Duration: 16 hours
Prerequisite: None
Course Outline:
Module 1: Introduction to Penetration Testing in Automotive Systems
Stages of Penetration Testing: Access, CAN Bus Access, Reverse Engineering, Attack Execution
Ethical Hacking Principles and Legal Considerations
Module 2: Accessing the Vehicle Systems
Techniques for Gaining Physical and Network Access
Security Implications and Strategies for Mitigating Risks
Module 3: Understanding CAN Bus Fundamentals
CAN Bus Architecture and Communication Protocols Explained
Vulnerabilities and Common Attack Vectors Targeting CAN Bus Systems
Module 4: Reverse Engineering the CAN Bus
Techniques and Tools for CAN Bus Analysis
Interpreting CAN Messages and Signals
Module 5: Practical Exercise: Simulated CAN Bus Penetration
Hands-on Activity: Conducting Penetration Testing in a Simulated Environment
Analysis and Discussion of Discovered Vulnerabilities
Module 6: Planning and Executing Penetration Tests
Developing a Comprehensive Penetration Testing Plan
Identifying Targets and Setting Objectives for Effective Testing
Module 7: Practical Penetration Testing in a Simulated Environment
Conducting Penetration Tests within a Controlled Simulation
Identifying and Exploiting Vulnerabilities in the Simulated System
Module 8: Transition to Real ECU Environment
Understanding ECU Characteristics and Security Features
Preparing for Penetration Testing in a Real-World Context
Module 9: Practical Exercise: ECU Penetration Testi
Hands-on Penetration Testing on Real Electronic Control Units
Assessing and Documenting Discovered Vulnerabilities
Module 10: Analyzing and Reporting Penetration Testing Results
Documenting Findings and Providing Recommendations for Mitigating Risks
Wrap-Up Session and Q&A to Address Participant Questions

Automotive Cybersecurity Crash Course
Start Date: August 28 - 29 2024
Time: 4 PM CET - 8 PM CET (4 hours each day)
Total Duration: 8 hours
Prerequisite: None
Course Outline:
Module 1: Introduction to Automotive Cybersecurity
Evolution of Automotive Cybersecurity
Current Landscape and Challenges
Module 2: Fundamentals of Cybersecurity
Key Concepts and Terminologies (CIA triad, vulnerabilities, threats)
Principles of Cybersecurity (defense in depth, risk management)
Module 3: Automotive Cybersecurity Fundamentals
Specifics of Cybersecurity in the Automotive Domain
Threat Landscape for Modern Vehicles (hacking, software exploitation)
Module 4: Introduction to ISO 21434 and UNECE Regulations
Overview of ISO 21434 and its objectives
Understanding UNECE Regulations in Automotive Cybersecurity
Module 5: Overview of ISO 21434
Key Elements of ISO 21434 (risk management, secure development lifecycle)
Implementation Strategies for ISO 21434
Module 6: Q&A
Module 7: Performing Threat Analysis & Risk Assessment (TARA)
Concept and Importance of TARA in Automotive Cybersecurity
ISO 21434 Approach to TARA
Identifying and Classifying Assets in an Automotive System
Assessing Asset Criticality
Identifying Potential Threats and Creating Threat Models
Analyzing Identified Threats and Vulnerabilities
Risk Evaluation and Treatment Strategies
Hands-On Exercise on Conducting TARA
Module 8: Practical Exercises and Wrap-Up
Recap of Key Learnings
Extended Q&A Session

Here's Peter, one of our graduates. See what he had to say about our training.
and Piotr...

Meet Praveen Gudi.
"I recently completed the Automotive Cybersecurity and Automotive Penetration Testing Course at Matrickz GmbH, and I highly recommend it to anyone interested in this growing field.
IN-DEPTH TRAINING
The course provided a comprehensive overview of automotive cybersecurity concepts and hands-on experience with penetration testing techniques. I particularly enjoyed the practical exercises that allowed us to apply the learned concepts to real-world scenarios.
CAREER ADVANCEMENT
This course has significantly enhanced my knowledge and skills in automotive cybersecurity. It has made me a more valuable asset to my current role and opened doors to new opportunities in the automotive security field.
HIGHLY RECOMMENDED
I would highly recommend this course to security professionals, automotive engineers, and anyone interested in gaining a deeper understanding of automotive cybersecurity threats and mitigation strategies."
What others are saying about us...

“Dr. Hasan Ibne Akram stands for extremely fast thinking, the special extra mile and high quality software.”

"My experience with Matrickz GmbH was always pleasant. The consultants and engineers of Matrickz GmbH provided services to my fullest satisfaction.”

“We have been cooperating successfully with Matrickz in software development for more than a year. This has brought us forward very quickly in the project work.”

"Valeo Powertrain Actuators Systems, in Ebern, was very satisfied with Matrickz. So there is nothing standing in the way of further collaboration in the future.”
Complete the course and get certified!


Looks interesting? What are you waiting for?
Jumpstart your automotive cybersecurity career and grab this life-changing opportunity today.
About Us
Discover Your Journey: Where Every Adventure Begins with Quality Essentials.
Contact Us
10785 W. Twain Ave. Ste 229, Las Vegas NV 89135
Phone: +49 177 5010543
Email: [email protected]






Facebook
Instagram
Youtube